When we think of a year wrap, we often think of Spotify Wrap, or maybe, if you’re more niche, LinkedIn or Duolingo wraps. In Science Discoveries 2025, however, the wrap looks very different.
Here, we give you our top 3 research wraps. From the immunology discovery that won the researchers a Nobel Prize, to stopping cancer in its tracks, to the drastic rise of diabetes and cardiovascular diseases because of sugary drinks.
The Immunology Discovery that Won the 2025 Nobel Prize!
The word “immunology” may bring up the instinct to skim the topic and move on to the next interesting read, but hear me out! Immunology is the study of the immune system, which is crucial to keeping you alive!
Think about it for a second. Isn’t it crazy how the immune system, essentially the security guards, can attack invaders while still recognizing and preventing damage to the body’s own cells?
When this fails to happen, autoimmune diseases arise. The term may seem unfamiliar to many, but diseases like type 1 diabetes, arthritis, multiple sclerosis, etc., are all autoimmune conditions, and they affect around one in ten people.
You probably know someone with these diseases. If yes, you also know that a cure is distant and difficult. However, a recent discovery has brought that dream much closer.
Key Discoveries in Immune Regulation
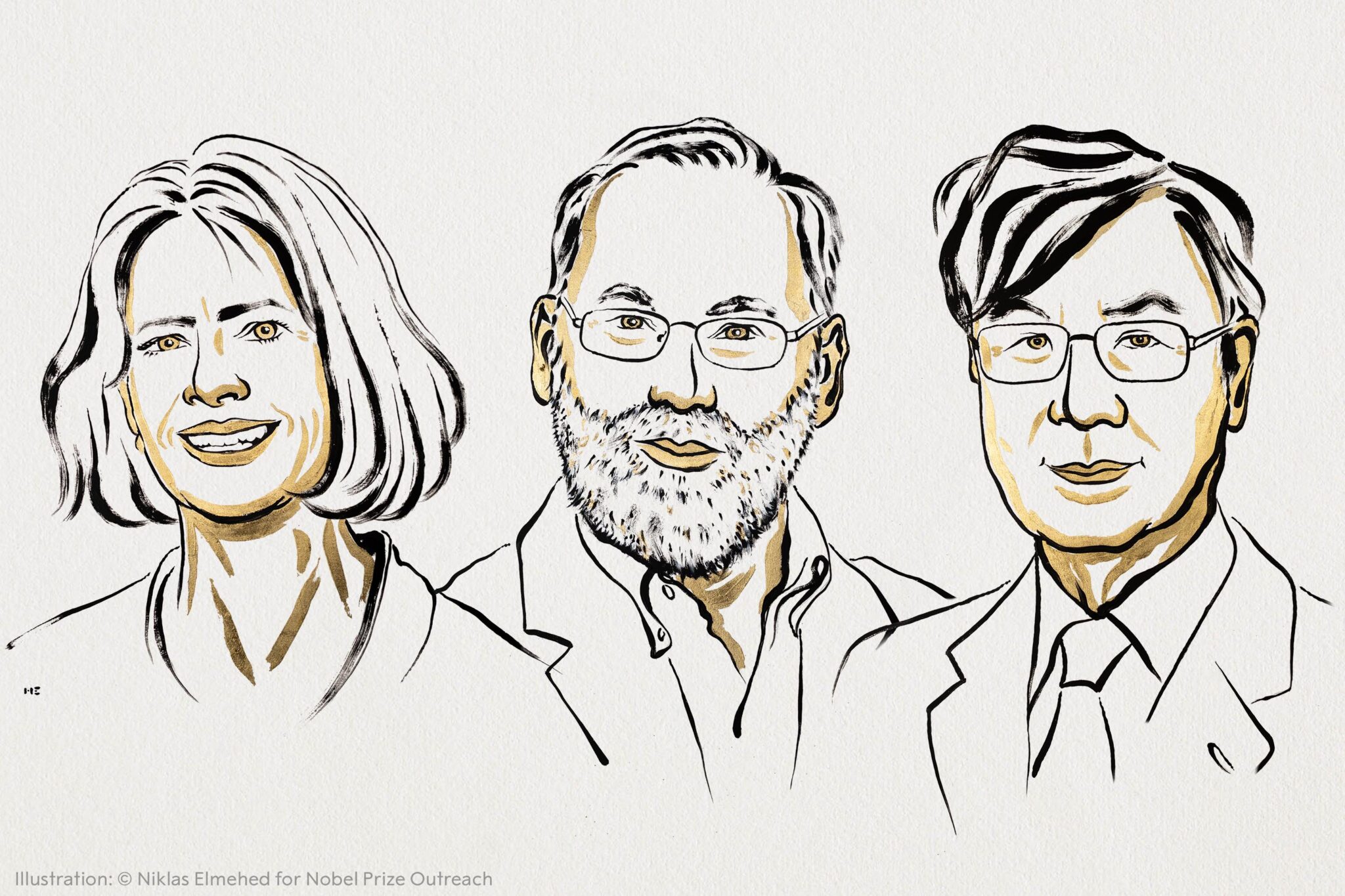
Mary Brunkow, Institute for Systems Biology in Seattle, Washington; Fred Ramsdell, Sonoma Biotherapeutics in Seattle, Washington; and Shimon Sakaguchi, University of Osaka in Suita, Japan, made a series of discoveries to solve this mystery.
This story starts with an unfortunate strain of mice termed the scurfy mouse, found in 1949. This mouse had an abnormal, unidentified X chromosome–linked mutation that causes severe autoimmune disease. This X-linked mutation meant that mice with the typical XY chromosomes were unable to survive, but females (XX) with a defective and a normal copy of the gene could survive.
This mouse was the reason we now understand that the Y chromosome is linked to maleness and was among the first discoveries on sex-linked genes. However, the reason for the abnormality was unknown, so the researchers kept the breed painstakingly alive for 300 generations.
This mutation was later found to be in Foxp3, which acts as a regulatory gene that, when mutated, fails to guide immune cells to the appropriate response. The immune cells in question are the T-regulatory cells (Tregs), which help suppress an overactive immune response. If Foxp3 is mutated, it is unable to tell the T-regulatory cells how to function, leading to a failed ‘brake’ response and an inability to prevent an overactive immune response.

Their discovery has been critical in understanding common diseases and is being used to discover new remedies for autoimmune diseases like lupus, type 1 diabetes, arthritis, etc.
Freezing Cancer Cells in their Tracks
“CELL”- The word brings images from class 6; a cell is a circular structure with a nucleus and different organelles that it holds in its tiny world. However, one may forget that there are different types of cells, each with its own unique shape—some thin and extended like neurons, or some flat and irregularly shaped like skin cells. These cells seem almost permanent in shape, but they are not the immobile blobs that we think they are.
How do cells move and adapt?
What makes them special is that they are able to move, alter their structure, and respond to their environment.
They do this with an internal cytoskeleton, which, much like our own, adds stability and structure. However, this cellular cytoskeleton isn’t made of calcium and bones; it’s made of proteins that assemble to form frames inside the cells, but also filaments or extensions outside the cell, like tiny hands or flippers.
These tiny hands shrink, grow, and shift positions depending on how the cell responds to external cues. In fact, cancer cells, when they begin metastasizing (migrating from one tumor lump to establish tumors in other parts of the body), use these very extensions to move away and into their new habitat.
Hence, these tiny hands are critical to understanding how cancer cells move around and how, in cancer therapy, they can be prevented.
Studying filopodia to stop cancer spread
Gregory M. Alushin published a paper in 2025 where he used cryo-electron microscopy, which flash-freezes cytoskeletal proteins to obtain a detailed view of proteins involved and how they interact with each other.
They highlight that these hand-like protrusions are called filopodia; they are made up of bundles or rods of actin, an abundant protein in the human body, that are glued together by another protein, fascin. How fascin helps assemble actin filaments was unknown before, and so Dr. Gregory and his team brought this to light. They find that fascin doesn’t grab actin rods the same way on either side; in fact, it has an almost unique ‘handshake’ that allows for a slightly lopsided linking of actin filaments.
Additionally, they found that a drug, G2, acts like a cap on fascin and prevents it from linking actin rods together. This is incredible because if fascin proteins no longer link actin rods, they can’t form the filopodia protrusions that help cells move around, offering a targeted strategy that could help stop cancer cells in their tracks.
The worrying link between diabetes, cardiovascular issues, and sugary drinks
As you walk into the familiarly decorated living rooms of your aunt or friend, you’re often asked the same question: “Kya len ge aap (what will you have) … Sprite, Coke, or water?” However, a recent study suggests that they may be better suited for offering diabetes.

Laura Lara-Castor and her team at the Friedman School of Nutrition Science and Policy at Tufts University link millions of cardiovascular and diabetes cases to the consumption of sugary drinks. In fact, they found that in Colombia, 48%, and in South Africa, 27.6%, of all new diabetes cases were linked to excess sugar in these drinks.
They explain that sugary beverages are digested rapidly, which may be beneficial in some situations, such as intensive sports, excessive amounts can lead to a sudden spike in blood sugar levels. They not only offer minimal nutritional value but are also reasons for excessive weight gain, insulin resistance, and multiple metabolic issues that are linked to cardiovascular diseases and type 2 diabetes.
The worrying thing is that these beverages are excessively sold in low- and middle-income countries without healthier or low-sugar alternatives. They become a natural choice for any meeting, guests, or events. Additionally, coupled with a lack of awareness about the detrimental effects of these drinks and a public system that isn’t equipped for their long-term consequences, a slippery slope is established that can easily lead to an increase in disease.
The paper suggests a multi-pronged approach to tackling this issue, ranging from public awareness campaigns, regulating the sale and advertisement of these sugary drinks, and actively offering other healthier alternatives sold as accessibly as these drinks currently are.
References:
- https://www.nature.com/articles/d41586-025-03193-3
- https://www.rockefeller.edu/news/38446-how-cells-move-and-change-shape-and-why-it-matters-for-our-health/
-
Fascinating structural plasticity mediates flexible actin bundle construction
- https://now.tufts.edu/2025/01/06/new-study-links-millions-diabetes-and-heart-disease-cases-globally-sugary-drinks
- Burdens of type 2 diabetes and cardiovascular disease attributable to sugar-sweetened beverages in 184 countries
More from the author: Tiny Giants: Bizarre and Mind-Blowing Tales from the Land of Ants!